
NASA Dryden Douglas Skyrocket
The Douglas Skyrocket (the D-558-2; also found, D-558-II) was a rocket and jet-powered research aircraft built by the Douglas Aircraft Company for the U.S. Navy. On November 20, 1953, shortly before the 50th anniversary of powered flight, Scott Crossfield piloted the Douglas D-558-2 Skyrocket to Mach 2, or more than 2076 km/h, the first time an aircraft had exceeded twice the speed of sound.
All three of the Skyrockets had 35-degree swept wings.
Until configured for air launch, NACA 143 featured a Westinghouse J-34-40 turbojet engine rated at 3,000 pounds force (13 kN) static thrust. It carried 260 US gallons (980 L) of aviation gasoline and weighed 10,572 pounds (4,795 kg) at take-off.
NACA 144 (and NACA 143 after modification in 1955) was powered by an LR-8-RM-6 rocket engine rated at 6,000 pounds force (27 kN) static thrust. Its propellants were 345 US gallons (1,306 L) of liquid oxygen and 378 US gallons (1,431 L) of diluted ethyl alcohol. In its launch configuration, it weighed 15,787 pounds (7,161 kg).
NACA 145 had both an LR-8-RM-5 rocket engine rated at 6,000 pounds force (27 kN) static thrust and featured a Westinghouse J-34-40 turbojet engine rated at 3,000 pounds force (13 kN) static thrust. It carried 170 US gallons (644 L) of liquid oxygen, 192 US gallons (727 L) of diluted ethyl alcohol, and 260 US gallons (984 L) of aviation gasoline for a launch weight of 15,266 pounds (6,925 kg).
[edit] Aircraft serial numbers
* D-558-2 Skyrocket
o D-558-2 #1 - #37973 NACA-143, 123 flights
o D-558-2 #2 - #37974 NACA-144, 103 flights
o D-558-2 #3 - #37975 NACA-145, 87 flights
* Maximum speed: 720 mph, 1,250 mph when air-launched (1,160 km/h, 2,010 km/h when air-launched)
* Stall speed: 160.1 mph (257.7 km/h)
* Service ceiling: 16,500 ft (5,030 m)
* Rate of climb: 22,400 ft/min, 11,100 ft/min under rocket power only (6,830 m/min., 3,380 m/min under rocket power only)
* Wing loading: 87.2 lb/ft² (426 kg/m²)
* Thrust/weight (jet): 0.39

















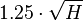 different arguments on average.
different arguments on average.






















